The DOJ has settled the sixth cybersecurity False Claims Act case in just eight months, marking fourteen settlements in less than four years since the DOJ launched its Civil Cyber-Fraud Initiative (CCFI). These settlements and the upcoming (and long-awaited) implementation of the CMMC program cement cybersecurity compliance as a DOJ enforcement priority and underscore the agency’s commitment to using the False Claims Act against contractors who fail to meet their cybersecurity obligations.
FCA Enforcement of Cybersecurity Compliance is on the Rise
Prior to the CCFI, there were only two public cybersecurity FCA cases—(1) the Cisco case, which was filed in 2011 and settled in 2019 for $8.6 million, and (2) the Aerojet case, which became public in 2017 and settled for $9 million just after the launch of the CCFI. Since 2023, cybersecurity FCA settlements have steadily trended upwards:
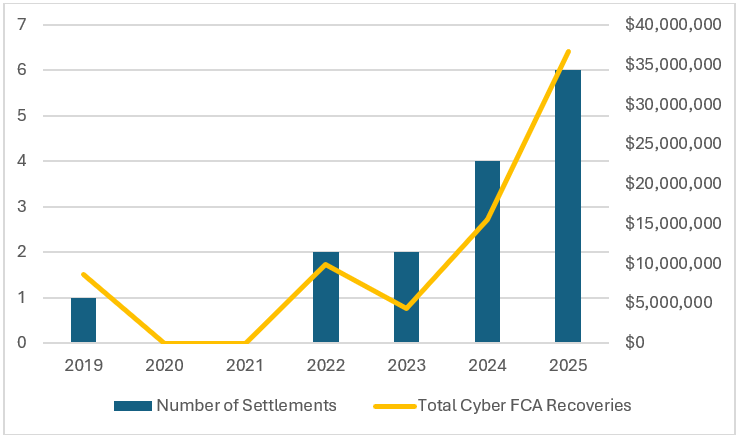
All told, cybersecurity FCA cases have recovered roughly $75 million for the government:
Many of the largest recoveries have come from whistleblower-initiated (aka qui tam) lawsuits—in the Guidehouse/Nan McKay, Illumina Inc., Raytheon, Aerojet, and Cisco cases.
Cybersecurity Enforcement Across Industries: From Healthcare to Defense
The six cybersecurity FCA settlements in 2025 span diverse industries—from healthcare administration and biotechnology to defense contracting and academic research—illustrating that cybersecurity compliance is critical across all sectors doing business with the federal government:
In more than one of these cases, the government alleged the defendant ignored cybersecurity risks flagged by third-party and/or internal auditors. Unfortunately, this is not uncommon in corporate environments. Whistleblower James Glenn was similarly ignored and then fired for flagging alleged cybersecurity vulnerabilities at Cisco. Another cybersecurity whistleblower, Andrew Harris, tried and failed to get Microsoft to address critical security vulnerabilities in its cloud infrastructure before the SolarWinds hack. These failures to heed internal reporting put us all at risk and expose companies that look the other way to liability under the FCA or securities laws.
We all benefit when companies implement robust whistleblower response systems. These systems should include dedicated reporting channels, cross-disciplinary review teams (to prevent information silos), clear timelines for investigating reported vulnerabilities, and transparent communication with internal reporters. Most critically, companies must prevent retaliation against internal reporters. By treating internal and external security warnings as valuable intelligence rather than unwelcome disruptions, organizations can address vulnerabilities before they escalate into enforcement actions or, more devastatingly, infiltrations that compromise the confidentiality, integrity, and availability of sensitive data.